EDISCOVERY AND DOCUMENT REVIEW PART II: Organizing Your Evidence & Protecting Privilege
Before we get too deep into our three part series on Protecting Privilege during Document Review, let’s ask, why is document review even necessary? According to to Rule 26 of the Federal Rules of Civil Procedure, any party may obtain discovery regarding any non-privileged information that is relevant to a legal claim or defense.
A document review is necessary because it not only distinguishes relevant data from irrelevant data, it also provides information and evidence about the issues of the matter and an opportunity to protect privileged material. In other words, the aims of review are sweeping, complicated, and sometimes contradictory.
To satisfy all of these facets, legal teams must make broad judgments while identifying specific issues; they have to bring important documents to light while suppressing others. It’s a balancing act, and can only be accomplished with careful organization and planning. This guide explains how to plan ahead and stay organized during review.
Structuring Privilege Review
The information in an ediscovery review set can be organized in many different ways:
-
- Chronologically
- By custodian
- By location
- By documents containing certain search terms
- Alphabetically
- By concept
- By email chains (sometimes called threads)
Search terms are used to help create a relevant review set or find particular issue-responsive files in the review set. But before you can estimate the costs and timeframe reliably, it is essential to design the structure of the review.
Before your review team tackles or divides tasks, they will need to think about:
-
- Number of reviewers and volume of evidence
- Complexity of the coding (number of tags the reviewers will be applying)
- Sophistication of the privilege issues presented by the facts of the case
- Number of passes of review that are anticipated
It’s a balancing act, and can only be accomplished with careful organization and planning.
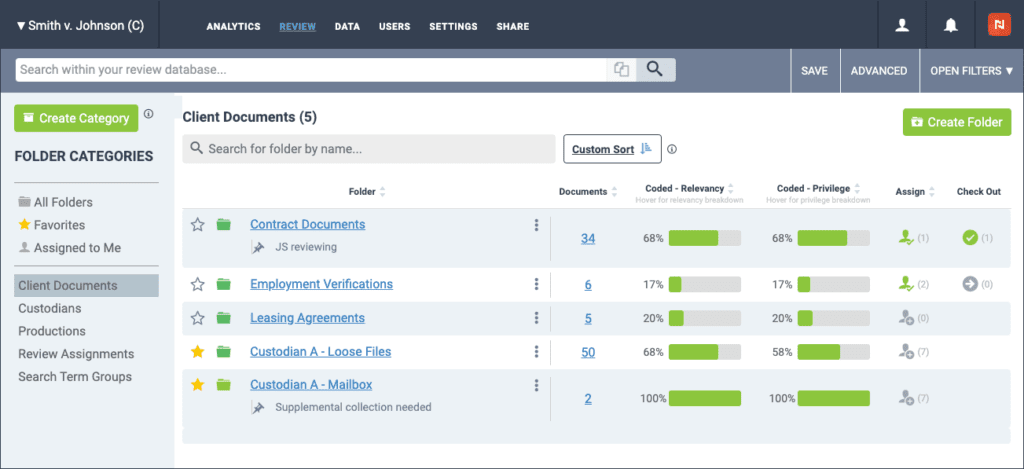
Use Folders to Stay Organized
As you can see above, Nextpoint software uses a folder structure. As your reviewers create collections of documents and evidence, they can easily organize it into folders, and they can organize those folders into categories. It’s much like a subfolder inside a folder on your desktop.
For example, you might create a category called Client Documents, and within that category organize folders like “Client Email Collection”, “Staffing Documentation”, “Contracts”, etc. As your project progresses, Folders can be used for production sets, witness folders, trial exhibits, and more.
Once reviewers have a collection of evidence to review, they can narrow the search if too many irrelevant documents are found. They can also broaden the search if too few relevant documents are found. They may add or remove search terms and use a variety of tools to locate responsive documents with minimal false positive search results.
When reviewing the data sets, make sure to analyze the efficiency and accuracy of search terms. This allows you to:
-
- Build a defensible privilege log
- Verify results to ensure quality control
- Communicate with partners and opponents
- Quality Control for a defensible review process
- Track Reviewer progress and adjust accordingly
As your team begins reviewing potentially responsive documents, they code them accordingly. For example, in a first pass review, they will use coding categories like Responsiveness, Responsive Issues, Confidentiality Designation, Privilege and Redaction Needed (usually related to Privilege).
 Reviewing for Attorney-Client Privilege
Reviewing for Attorney-Client Privilege
Our recommended best practice for privilege review is to search the review data set using a list of search terms that will likely identify privileged documents. Be sure to provide all reviewers with a list of people and topics that may involve privilege.
Some potential search terms for privileged documents include:
-
- Names and internet domains of in-house and outside counsel, paralegals, and other legal staff
- Legal words such as deposition, subpoena, interrogatory, privileged language (i.e., “produced for settlement discussion purposes only”)
A privilege log describes documents or other items withheld from production under claims such as attorney-client privilege, work product doctrine, or trade secrets. When documents have been tagged and coded properly, ediscovery tools should be able to assist in the production of the privilege log.
Be aware that courts may not accept the results of certain technology assisted review. At your Meet and Confer with opposing counsel, discuss and agree on the review methodology to avoid problems in court. It is useful to have a skilled project manager with experience in the tools, processes and technologies to ensure repeatable, defensible results.
Protecting Attorney-Client Privilege
A failure to protect privilege can be devastating to a case. All team members should be aware of their roles and responsibilities.
COUNSEL:
Counsel should review the court’s requirements for a privilege log (e.g., level of detail needed, specific information).
REVIEW TEAM:
Once the review team understands the facts and documents they will be responsible for the privilege log creation.
QUALITY CONTROL:
Identify team members who will manage Quality Control and transparency (i.e., workflow, how the documents were identified, and collection methods) to provide the needed level of defensibility to the privilege log.
After the first level review is conducted, privileged documents are marked. These documents should be re-checked with a critical eye, so that documents that are not truly privileged – and are responsive to the discovery request – are removed from the privileged log and appropriately designated for production. Any privileged documents that have not been marked – but should be – need to be identified as privileged and included in the privilege log.
The Ediscovery Document Review Challenge
Ediscovery is an enormous challenge that can frustrate even experienced project managers. Processing and making millions of documents searchable, dealing with indeterminate files types, protecting privilege, and keeping it all organized is a formidable technical challenge. And don’t forget, there’s an opposing party that may challenge every document produced, every disclosure made, every claim, response, or choice your team makes.
Expand Your Knowledge on Ediscovery Document Review
Check out Parts 1 and 3 of our Ediscovery Document Review Series:
-
- Ediscovery Document Review: Strategy Is Half the Battle outlines the strategic aspects of review planning
- Ediscovery Document Review: Getting Results explains how to conduct effective searches
And download our comprehensive document review eGuide
 If you’re looking for help with any legal review process, please reach out to the experts at Nextpoint. They can assist with any matter, big or small, from specific technical questions to big picture review strategies.
If you’re looking for help with any legal review process, please reach out to the experts at Nextpoint. They can assist with any matter, big or small, from specific technical questions to big picture review strategies.