Recently, I’ve been asking law firms to defend their decision to continue storing client and firm data on premise. The most common defense I hear from firms is that it’s risky to put it in the cloud, where it is “potentially at risk of being hacked.”
Essentially, the pervasive belief in law firm data security is that there’s no one actively attempting to get at this data from the outside, so it’s “secure enough” on premise. Er, no.
No. Your Data Is Not Secure Enough
This on-premise argument has two fatal flaws.
First, if an on-premise network is connected to the Internet, then the data is at much greater risk than encrypted data stored in a secured cloud facility. Hackers attack via the Internet. Law firms simply can’t invest in the caliber of resources needed, or home-grow the expertise needed to securely host data that is exposed to the Internet. It’s not a realistic expectation.
Second, this argument relies on the assumption that a law firm’s current data security model is adequate. “We don’t need to do more, what we do currently is enough.” After all, who would be interested in a law firm’s data?
The “who” are all parties adverse to your client. Lawyers relying on the ethical rules bounding legal practice and the potential civil and criminal penalties for hacking an opponent do have a safeguard – but is that “enough?” You’re essentially assuming your adversaries are as ethical as you.
But is this a rational or defensible approach? After all, a private investigator recently plead guilty to charges he was regularly paying commercial hackers. The PI, Eric Saldagga, has 19 law firms listed on his company’s website as clients. So while the firm on the other side may be ethical , there are more potential threats than just your opposing law firm.
The implications for litigators are significant. Unless you conclude there is zero probability of parties adverse to your client snooping on your law firm network in order to gain an advantage during litigation, then you have a professional obligation to do more than you are doing today.
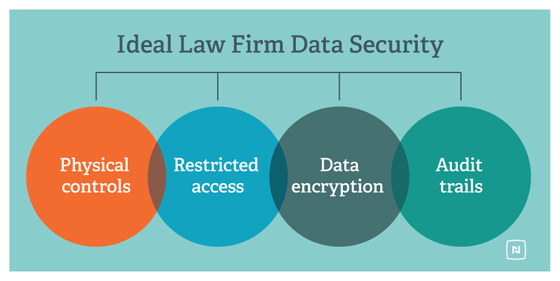
Best practices today for law firms addressing data security fall broadly into four critical areas:
- Physical and Environmental Controls
- “Need to Know” Access Within the Law Firms
- Encryption and User Authentication
- Audit trail and Access Logs
1. Physical & Environmental Controls in Data Storage
This article from Enterprise Storage Forum has a good summary of the major issues with physically securing data. The article outlines three main threats to the data center: physical intrusion, natural disaster, and energy issues.
Physical Intrusion: Data stored on-premise at a law firm has significant exposure. Cleaning staff, non-critical employees with access, burglary threats – these are very real exposure points. Best practice is to have HQ separate from the data center. And, for that data center to be in a low-denisty area, not in the center of an urban area with lots of people around.
Natural disasters: A rapidly increasing concern. Just ask Hoboken residents after Superstorm Sandy.
Energy issues: Heating, cooling, and redundant power sources in the event of an energy grid disruption are all significant considerations that make off-site storage of law firm client data compelling.
2. “Need to Know” Data Access Within Law Firms
Many law firm networks permit users to access all of the data within the firm’s network. This exposes firms to bad actors within their firms. Best practices are to restrict access to data particular to a matter only to those individuals critical to that matter.
Restricting data access to firm staff actively working on a matter is a sensible, obvious step to increasing the overall data security practices inside a firm.
3. Data Encryption & User Authentication
A recent article from the Law Practice Today recommends encryption as the first step to take. The lack of encryption by the largest Blue Cross organization has become a significant issue after 80 million records were compromised.
Encryption of data in transit is the lowest standard that firms should adhere to. But, encryption of data at rest and in transit should be the targeted goal to achieve. If not today, then in the very near future.
What’s more, institutionalizing two factor authentication for users is the minimum ante for law firms, as it is for financial information and health care information.
4. Data Audit Trail & Access Logs
When looking at the panoply of data security standards propagated – Sarbanes-Oxley, HIPAA, PCI-DSS, ISO27001, SOC3, FISMA – a consistent and required practice is the ability to document who accessed data, what data they accessed, and when they accessed it.
It just makes sense. If your firm is the victim of a breach, the ability to define exactly what data was exposed, to whom, and when, will be of critical importance. Being proactive about getting systems, technology and processes in place to easily surface a definitive audit trail and access log is an absolute must.
“Good enough” in law firm data security should include (at the very least): Robust physical and environmental controls, restricted data access, data encryption at rest and in transit, and detailed audit trails and access logs. Does your law firm’s on premise data storage program meet these criteria?