We covered some diverse ground on the Nextpoint blog in 2015, publishing 23 legal technology stories that ranged from dissecting new laws and trends, outlining best practices in eDiscovery, and teaching legal professionals how to work more efficiently with the aid of software.
In case you missed them, here are summaries of our five most popular stories of the year.

7 Characteristics of Law Firms That Are Legal Technology Rockstars
Nextpoint CEO Rakesh Madhava identifies the traits that differentiate law firms who excel at using technology to win more cases and clients. In short, he argues that these traits all stem from a hands-on learning approach to legal tech that becomes embedded in a firm’s culture. Read the post »

5 Experts Predict How the 2015 FRCP Rules Will Impact Discovery
In December, U.S. district courts adopted the first amendments to the Federal Rules of Civil Procedure since 2007. We rounded up five influential eDiscovery speakers, including Craig Ball and Ricoh’s David A. Greetham, to share their thoughts on how the new language would alter the practice of litigation in the years to come. Some opinions were different than you might expect. Read the post »
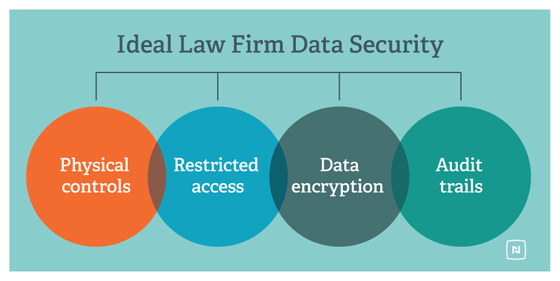
4 Critical Data Security Tips for Law Firms
Learn the best practices law firms must follow to responsibly protect their clients’ data—and their own—from hackers who want to steal it. Rocky also exposes flaws in the popular myth that client data is easier to secure in on-site server networks than in the cloud. Read the post »

What Every Lawyer Needs to Know About Native Files
While most document review work is done with rendered copies of digital evidence, the original source (or “native”) files still have an important role to play in discovery. Learn more about what native files are, why you might need them and how to make them accessible to your team. Read the post »

5 Lessons from the Anthem Security Breach
What can litigators learn from one of the largest breaches of sensitive personal information in American history? Start with the notion that it could just as easily happen to you. Then take specific actions to protect your clients’ data. Read the post »







