DESKTOP & TABLET
TRUSTED EDISCOVERY SECURITY & COMPLIANCE
Rest easy with the strictest data security standards.
MOBILE
TRUSTED eDiscovery SECURITY & COMPLIANCE
Rest easy with the strictest data security standards.
Keeping your data secure, confidential and accessible
An AWS technology partner since 2005, our data security provisioning is long-proven and without peer.
DESKTOP & MOBILE
TABLET LANDSCAPE PORTRAIT
DESKTOP
Download the Nextpoint Security and Privacy Overview.
TABLET LANDSCAPE
Download the Nextpoint Security and Privacy Overview.
TABLET PORTRAIT
Download the Nextpoint Security and Privacy Overview.
MOBILE
Download the Nextpoint Security and Privacy Overview.
DESKTOP & TABLET LANDSCAPE
For more than 13 years Nextpoint has been hosted by Amazon Web Services. The AWS global cloud-computing infrastructure is managed according to the strictest standards of security and compliance, and trusted by NASA, the CIA and many leading corporations.
Read the 2010 Nextpoint Case Study written by AWS. (Yeah, we’ve been doing this best-in-class security thing a long time!)
TABLET PORTRAIT & MOBILE
For more than 13 years Nextpoint has been hosted by Amazon Web Services. The AWS global cloud-computing infrastructure is managed according to the strictest standards of security and compliance, and trusted by NASA, the CIA and many leading corporations.
Read the 2010 Nextpoint Case Study written by AWS. (Yeah, we’ve been doing this best-in-class security thing a long time!)

DESKTOP & TABLET LANDSCAPE
Whether in motion or at rest, our best in class SSL encryption (SHA-256, 256-bit keys) keeps your data unreadable to unauthorized parties—even in the unlikely event that physical access to the data was somehow gained.
Comprehensive Audit Trails
Comprehensive audit trails and reporting features ensure you know who has accessed each and every document.
TABLET PORTRAIT & MOBILE
Whether in motion or at rest, our best in class SSL encryption (SHA-256, 256-bit keys) keeps your data unreadable to unauthorized parties—even in the unlikely event that physical access to the data was somehow gained.
Comprehensive Audit Trails
Comprehensive audit trails and reporting features ensure you know who has accessed each and every document.
DESKTOP & TABLET LANDSCAPE
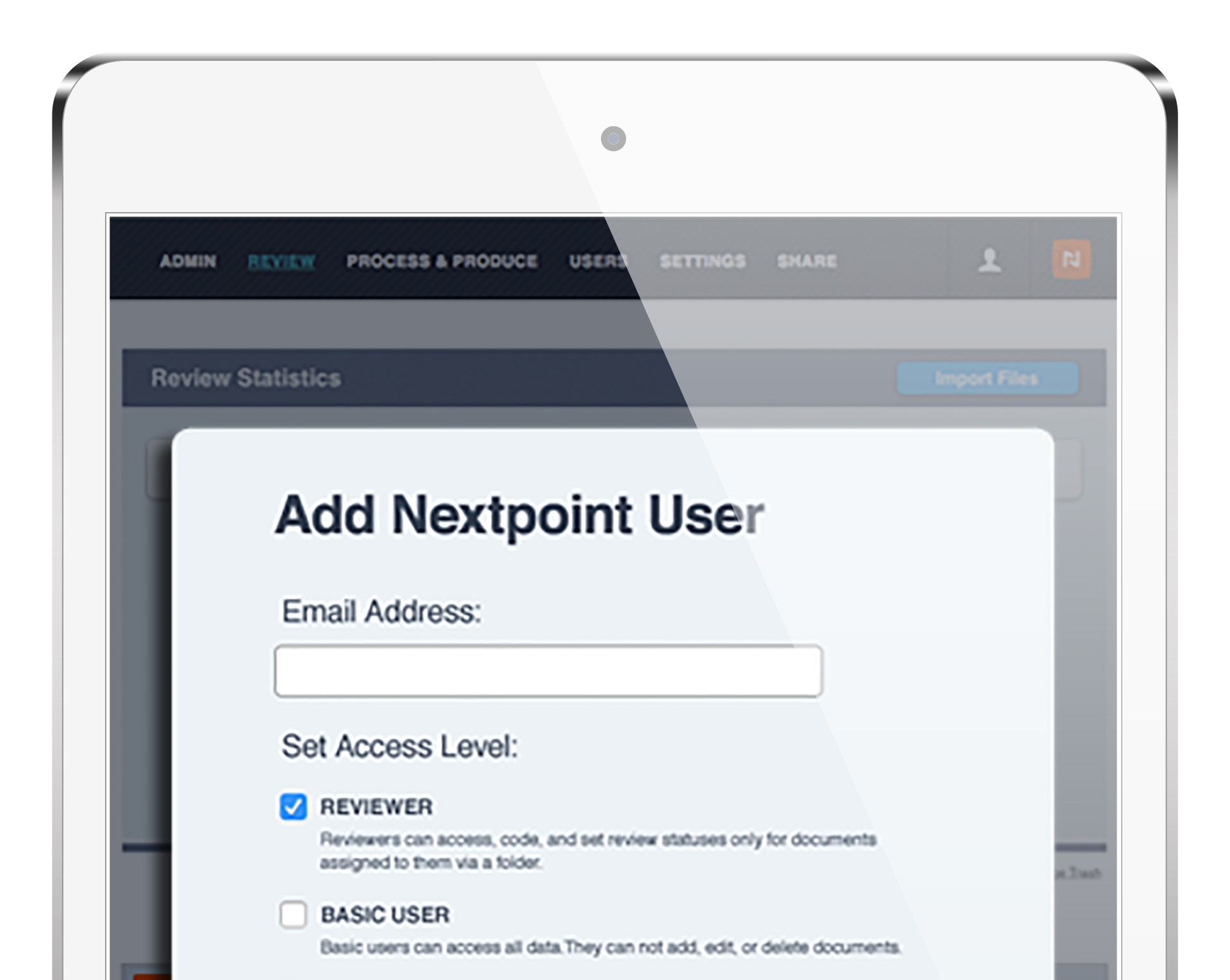
Access to data is permissions-based. Four distinct “clearance” levels assigned to users based on role—mean you control who can access data at the case, folder and document level.
Forced two-factor user authentication
Just one more level of protection Nextpoint demands to ensure the privacy of your confidential data.
TABLET PORTRAIT & MOBILE
Access to data is permissions-based. Four distinct “clearance” levels assigned to users based on role—mean you control who can access data at the case, folder and document level.
Forced two-factor user authentication
Just one more level of protection Nextpoint demands to ensure the privacy of your confidential data.

DESKTOP & TABLET LANDSCAPE

As a founding member of the Legal Cloud Computing Association, we take cloud data security very seriously. More seriously than other cloud services—and in fact—more seriously than most law firms do.
That’s why we co-authored the industry’s first set of cloud security standards crafted specifically for the legal industry.
TABLET PORTRAIT & MOBILE

As a founding member of the Legal Cloud Computing Association, we take cloud data security very seriously. More seriously than other cloud services—and in fact—more seriously than most law firms do.
That’s why we co-authored the industry’s first set of cloud security standards crafted specifically for the legal industry.
"You can pull it up on any tablet, ipad, or computer and the two-factor security gives me and my clients peace of mind. New updates keep making it easier to use as well."
“You can pull it up on any tablet, ipad, or computer and the two-factor security gives me and my clients peace of mind. New updates keep making it easier to use as well.”
 Nina Towle Herring, Cory Watson Attorneys
Nina Towle Herring, Cory Watson Attorneys
LEARN MORE ABOUT OUR UNMATCHED EDISCOVERY SECURITY
Trusted by some of the world’s smartest law firms